RPISEC Kernel Challenge
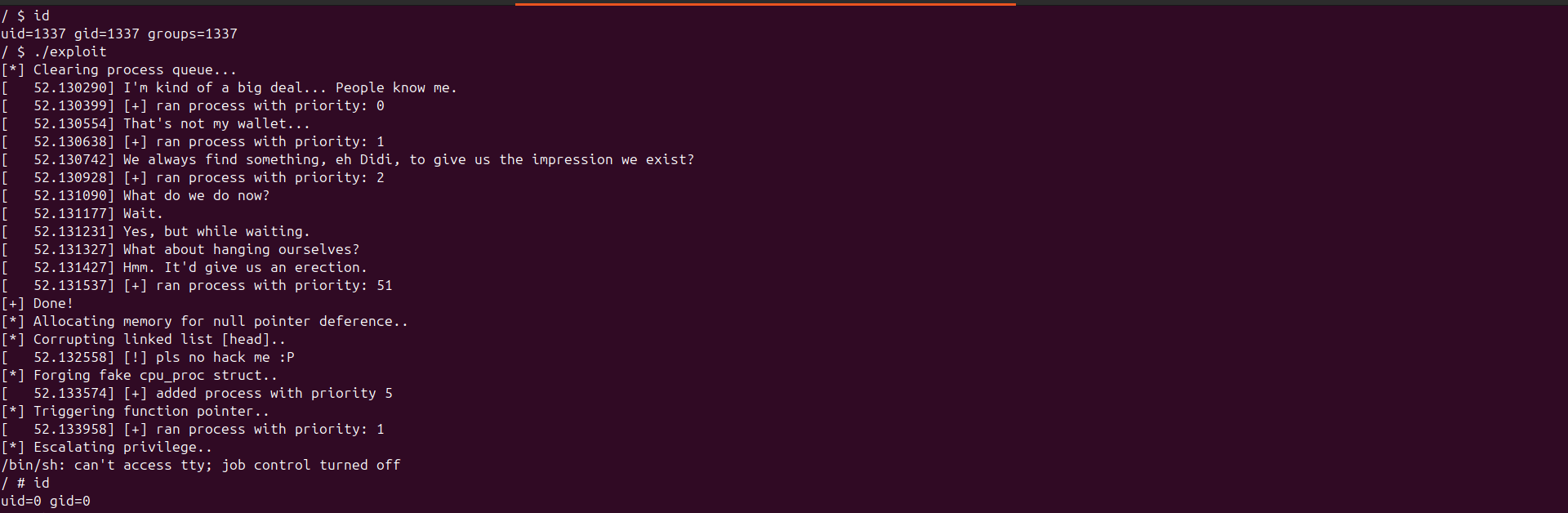
RPISEC Kernel Exploitation Overview After watching the video on kernel exploitation, I decided to take things further by attempting chall1, the challenge provided by the organizers for viewers to...

RPISEC Kernel Exploitation Overview After watching the video on kernel exploitation, I decided to take things further by attempting chall1, the challenge provided by the organizers for viewers to...
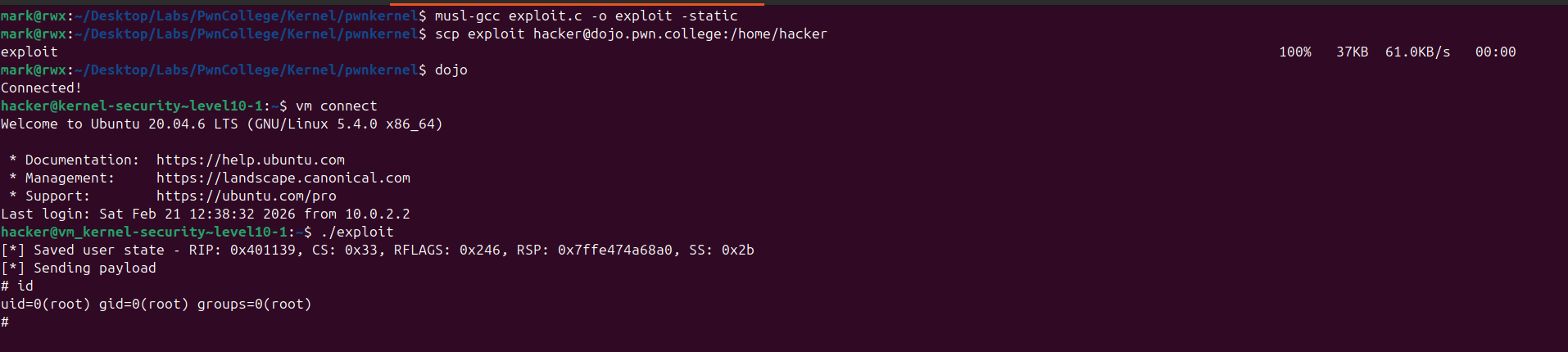
Kernel Security Overview Having completed the Kernel Security module at pwn.college, I decided to document my approach to the Level 10 challenge. Interestingly, I solved it using a method differ...
NahamCon Winter CTF 2025 Overview This writeup covers all pwn challenges from NahamCon Winter CTF 2025. The event featured two pwnable challenges: VulnBank Snorex VulnBank Challenge Infor...
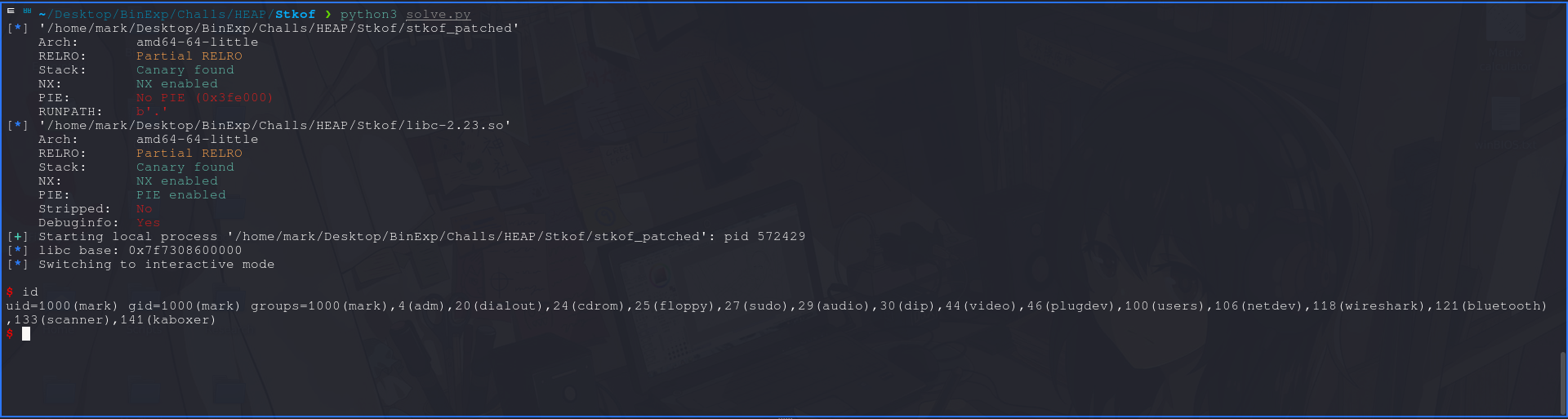
STKOF Overview STKOF is a classic heap exploitation challenge from HITCON CTF 2014, targeting glibc 2.23. The binary contains a heap-based overflow vulnerability that allows corruption of adjacen...

Dreamhack - Tiny Machine Overview The Tiny Machine challenge implements a simple 8-bit register-based virtual machine written in Python. The VM loads the flag into memory, allocates space for our...

International Cybersecurity Challenge (ICC) - Tokyo Japan In this blog post, I’ll be sharing my personal experience as a first time participant of the International Cybersecurity Challenge (ICC) d...
First Blog Post Phew! I finally decided to update this blog. If you’ve seen my blog before, you’d know I had quite a few writeups here… sadly, I lost most of them. Things didn’t go exactly as I ...